阿里云通过一台公网IP地址,让其他内网机器访问互联网
在公网IP这台机器上执行(172.17.127.215不能访问外网的ip,172.17.127.214可以访问外网的IP)注:开启了路由转发功能,可能会影响到某些部署的应用,例:Grafana会访问报错。打开专有网络---路由表---实例名称---添加路由条目。#ping通表示内网ECS实现对外资源访问了。在有公网的ECS上操作。
1、开启ECS的路由转发功能
在有公网的ECS上操作
# echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
# sysctl -p
注:开启了路由转发功能,可能会影响到某些部署的应用,例:Grafana会访问报错。
2、配置IPTABLES的NAT转发规则
在公网IP这台机器上执行(172.17.127.215不能访问外网的ip,172.17.127.214可以访问外网的IP)
[root@test1 config]# iptables -t nat -A POSTROUTING -s 172.17.127.0/24 -o eth0 -j SNAT --to-source 8.148.5.173
[root@test1 config]# iptables -t nat -I POSTROUTING -s 172.17.127.215/32 -j SNAT --to-source 172.17.127.214
[root@test1 config]# iptables -t nat -L
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DOCKER all -- anywhere anywhere ADDRTYPE match dst-type LOCAL
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.17.127.215 anywhere to:172.17.127.214
MASQUERADE all -- 172.18.0.0/16 anywhere
MASQUERADE all -- 172.19.0.0/16 anywhere
MASQUERADE tcp -- 172.18.0.2 172.18.0.2 tcp dpt:EtherNet/IP-1
MASQUERADE tcp -- 172.19.0.2 172.19.0.2 tcp dpt:mysql
MASQUERADE tcp -- 172.18.0.2 172.18.0.2 tcp dpt:http
MASQUERADE tcp -- 172.19.0.3 172.19.0.3 tcp dpt:redis
MASQUERADE tcp -- 172.19.0.4 172.19.0.4 tcp dpt:vrace
MASQUERADE tcp -- 172.19.0.5 172.19.0.5 tcp dpt:8848
MASQUERADE tcp -- 172.19.0.4 172.19.0.4 tcp dpt:wap-wsp
MASQUERADE tcp -- 172.19.0.6 172.19.0.6 tcp dpt:8099
MASQUERADE tcp -- 172.19.0.7 172.19.0.7 tcp dpt:opsmessaging
MASQUERADE tcp -- 172.19.0.8 172.19.0.8 tcp dpt:8093
MASQUERADE tcp -- 172.19.0.9 172.19.0.9 tcp dpt:8092
MASQUERADE tcp -- 172.19.0.10 172.19.0.10 tcp dpt:8096
MASQUERADE tcp -- 172.19.0.11 172.19.0.11 tcp dpt:8094
MASQUERADE tcp -- 172.19.0.12 172.19.0.12 tcp dpt:jamlink
MASQUERADE tcp -- 172.19.0.13 172.19.0.13 tcp dpt:8095
MASQUERADE tcp -- 172.19.0.14 172.19.0.14 tcp dpt:vce
MASQUERADE tcp -- 172.19.0.14 172.19.0.14 tcp dpt:sd
MASQUERADE tcp -- 172.19.0.14 172.19.0.14 tcp dpt:us-cli
MASQUERADE tcp -- 172.19.0.14 172.19.0.14 tcp dpt:https
MASQUERADE tcp -- 172.19.0.14 172.19.0.14 tcp dpt:http
SNAT all -- 172.17.127.215 anywhere to:8.148.5.173
SNAT all -- 172.17.127.0/24 anywhere to:8.148.5.1734、配置阿里云控制台
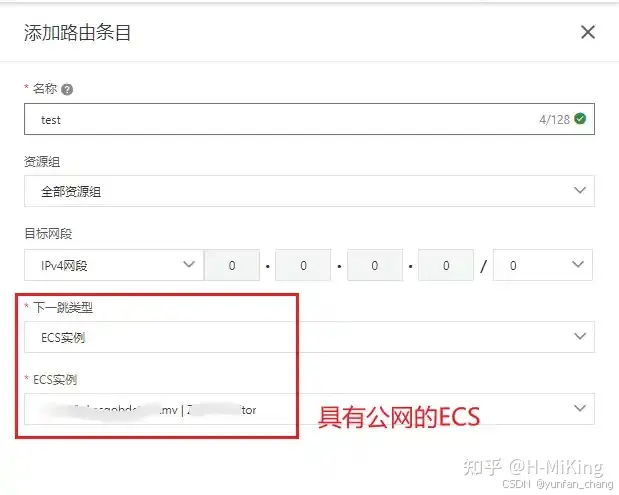
打开专有网络---路由表---实例名称---添加路由条目
5、测试
# ping www.jd.com
PING jd-abroad.cdn20.com (222.132.143.108) 56(84) bytes of data.
64 bytes from 222.132.143.108 (222.132.143.108): icmp_seq=1 ttl=48 time=32.0 ms
64 bytes from 222.132.143.108 (222.132.143.108): icmp_seq=2 ttl=48 time=32.0 ms
64 bytes from 222.132.143.108 (222.132.143.108): icmp_seq=3 ttl=48 time=32.0 ms
# ping通表示内网ECS实现对外资源访问了。
更多推荐
 已为社区贡献3条内容
已为社区贡献3条内容









所有评论(0)