阿里云与Let‘s Encrypt生成通配符证书的使用
前言每个阿里云账户的免费证书有可能存在不够使用的情况,为了能够继续使用免费证书保障网站的安全性,可以使用Let’s Encrypt,满足我们的需求操作流程安装certbot-auto生成证书工具本作者是在centos7.x系统是操作,可在公司内网,亦可在各大云厂商的服务器上yum -y install epel-releaseyum -y install certbot生成通配符域名证书certb
·
前言
每个阿里云账户的免费证书有可能存在不够使用的情况,为了能够继续使用免费证书保障网站的安全性,可以使用Let’s Encrypt,满足我们的需求
操作流程
安装certbot-auto生成证书工具
本作者是在centos7.x系统是操作,可在公司内网,亦可在各大云厂商的服务器上
yum -y install epel-release
yum -y install certbot
生成通配符域名证书
一.输入如下命令进入相关操作指引:
~]# certbot-auto certonly -d *.xxx.xxx --manual --server https://acme-v02.api.letsencrypt.org/directory
/usr/local/bin/certbot-auto has insecure permissions!
To learn how to fix them, visit https://community.letsencrypt.org/t/certbot-auto-deployment-best-practices/91979/
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for ecaiedu.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y # 输入值:Y:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.xxx.com with the following value:
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx # 此字符串请记住,是用于填写下一步骤的域名解析的txt记录值
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue # 请不要按键,先完成下一步骤,至关重要
- 注:
- 在此过程如遇到输入你的邮箱,请输入你的邮箱联系方式,方可进入下一步操作,本作者制作此文档时,已查询不到相关记录,请自行留意命令行输出
- ✳.xxx.xxx,eg:✳.nature.com,域名需是你公司或者个人的域名,并能解析
二.阿里云域名解析txt记录
操作可参考如下所示: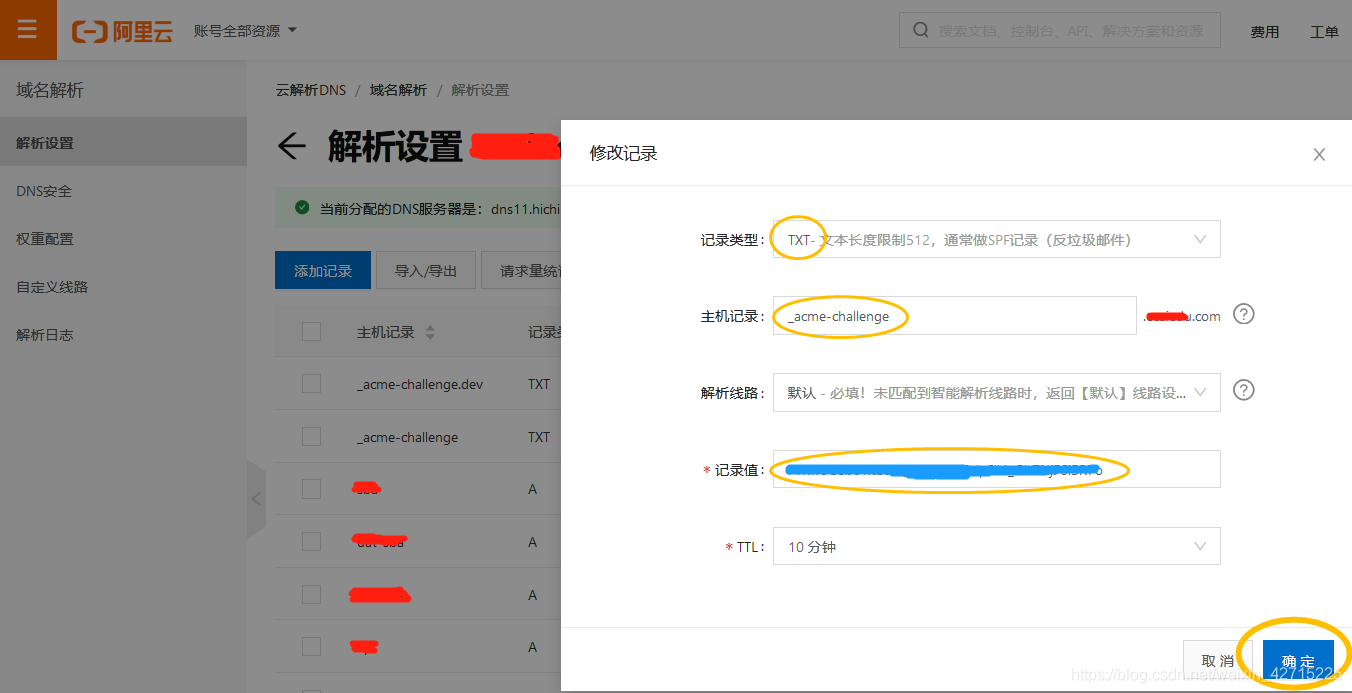 三.win系统下终端命令行nslookup查询域名解析情况
三.win系统下终端命令行nslookup查询域名解析情况
操作如下:
C:\WINDOWS\system32>nslookup
默认服务器: UnKnown
Address: 192.168.110.19 # 此为本文作者公司内网coredns的ip
> set type=txt # 输入此内容
> _acme-challenge.xxx.com # 输入第一步骤产生的DNS TXT name
服务器: UnKnown
Address: 192.168.110.19
非权威应答:
_acme-challenge.ecaiedu.com text =
"xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" # 当有此值输出,并与第一步骤产生的DNS TXT value一致时,表示完成解析,可以在万网的情况下,访问到相应的域名服务
ecaiedu.com nameserver = dns11.hichina.com
ecaiedu.com nameserver = dns12.hichina.com
dns11.hichina.com internet address = 140.205.81.15
dns11.hichina.com internet address = 140.205.81.25
dns11.hichina.com internet address = 106.11.141.115
dns11.hichina.com internet address = 106.11.141.125
dns11.hichina.com internet address = 106.11.211.55
dns11.hichina.com internet address = 106.11.211.65
dns11.hichina.com internet address = 140.205.41.15
dns11.hichina.com internet address = 140.205.41.25
dns12.hichina.com internet address = 140.205.81.26
dns12.hichina.com internet address = 106.11.141.116
dns12.hichina.com internet address = 106.11.141.126
dns12.hichina.com internet address = 106.11.211.56
dns12.hichina.com internet address = 106.11.211.66
dns12.hichina.com internet address = 140.205.41.16
dns12.hichina.com internet address = 140.205.41.26
dns12.hichina.com internet address = 140.205.81.16
dns11.hichina.com AAAA IPv6 address = 2400:3200:2000:30::1
dns12.hichina.com AAAA IPv6 address = 2400:3200:2000:31::1
四.生成通配符证书
当完成二、三步骤后,进入如下操作(终端输出续上)
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue # 请输入任意键继续
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/xxx.com/fullchain.pem # 公钥,请记住并留存好
Your key file has been saved at:
/etc/letsencrypt/live/xxx.com/privkey.pem # 私钥,请记住并留存好
Your cert will expire on 2020-10-22. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
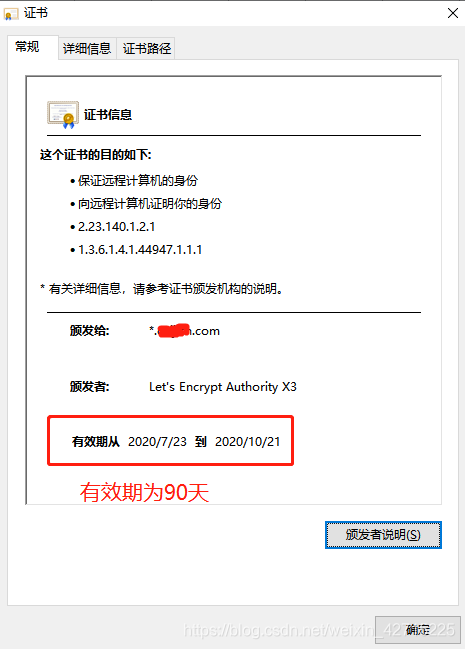
此时已生成了关于*.nature.com的通配符域名证书,相关域名,eg:dev.nature.com、uat.nature.com、prod.nature.com等域名可以共用此证书
证书配置
常规方式部署的ng配置证书
此只记录ng配置证书的的部分内容,其它环节请自行完成,已使你的web网站是443的安全网站
cat > /etc/nginx/conf.d/ngone.conf <<-EOF
upstream ngone{
server 127.0.0.1:8060;
}
server {
listen 80;
server_name ngone.nature.com;
rewrite ^/(.*)$ https://ngone.nature.com/$1 permanent;
}
server {
listen 443;
server_name ngone.nature.com;
ssl on;
ssl_certificate cert_auth/xxx.com.pem; # 其内容为生成的文件:/etc/letsencrypt/live/xxx.com/fullchain.pem
ssl_certificate_key cert_auth/xxx.com.key; # 其内容为生成的文件:/etc/letsencrypt/live/xxx.com/privkey.pem
ssl_session_timeout 5m;
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!NULL:!aNULL:!MD5:!ADH:!RC4;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
access_log /var/log/nginx/ngone/access.log main;
error_log /var/log/nginx/ngone/error.log;
location / {
proxy_pass http://ngone;
proxy_redirect off;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
EOF
- 注:
阿里云控制台上进行添加域名解析后,访问其web网站,可参考如下效果所示: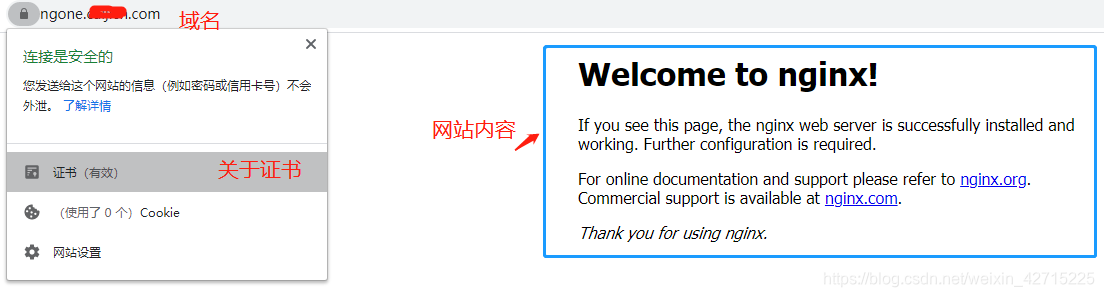
k8s配置通配符域名证书
- 1.文件目录树如下所示:
~]$ tree -aCg nature/
nature/
├── [nature ] certs # 存放证书目录
│ ├── [nature ] tls-nature.com.key # 其内容为生成的文件:/etc/letsencrypt/live/xxx.com/privkey.pem
│ └── [nature ] tls-nature.com.pem # 其内容为生成的文件:/etc/letsencrypt/live/xxx.com/fullchain.pem
└── [nature ] tls-nature-dev.sh # 创建k8s的secret的通配符证书脚本
1 directory, 3 files
- 2.脚本文件
cat > nature/tls-nature-dev.sh <<-EOF
#!/usr/bin/env bash
kubectl create secret tls tls-natureu.com -n dev \
--cert=certs/tls-nature.com.pem \
--key=certs/tls-nature.com.key
EOF
- 3.部署关于k8s在dev命名空间下的通配符域名证书的secret
bash nature/tls-nature-dev.sh
结语
… …
更多推荐
 已为社区贡献4条内容
已为社区贡献4条内容








所有评论(0)