SM2 密钥协商-openssl代码测试
SM2 密钥交换协议 opensslC语言代码
·
SM2 密钥协商-openssl代码测试
简介
SM2密钥协商,即密钥交换流程,满足《GMT 0003.3-2012 SM2椭圆曲线公钥密码算法第3部分:密钥交换协议》协议规范要求,是通信双方通过密钥交换流程,协商出一个共同的会话密钥。在国密TLS流程中ECDHE-SM4-SM3 套件就是用到了SM2的密钥交换流程。
SM2密钥协商流程
SM2密钥交换流程如下:
密钥协商源码
发起方A
EC_POINT *gen_agreementdata(SM2KA *ka)
{
ka->r = BN_new();
#if 0
BN_rand_range(ka->r, ka->order);
#else
BN_bin2bn(r_a, 32,ka->r);
#endif
ka->R = EC_POINT_new(ka->group);
EC_POINT_mul(ka->group, ka->R, ka->r, NULL, NULL, ka->ctx);
dump_bn("ra:",ka->r);
printf("点RA\n");
dump_point(ka, ka->R);
return ka->R;
}
响应方B
EC_POINT *gen_agreementdata_key(SM2KA *ka, EC_POINT *RA, EC_POINT *PA, unsigned char *Z_peer)
{
EC_POINT *ret=NULL;
ka->r = BN_new();
#if 0
BN_rand_range(ka->r, ka->order);
#else
BN_bin2bn(r_b, 32,ka->r);
#endif
ka->R = EC_POINT_new(ka->group);
EC_POINT_mul(ka->group, ka->R, ka->r, NULL, NULL, ka->ctx);
dump_bn("rb:",ka->r);
printf("点RB\n");
dump_point(ka, ka->R);
BIGNUM *x = BN_new();
BIGNUM *t = BN_new();
calc_x(ka, ka->R, &x);
dump_bn("x2`:",x);
BN_mod_mul(t, x, ka->r, ka->order, ka->ctx);
BN_mod_add(t, t, ka->prik, ka->order, ka->ctx);
dump_bn("tb:",t);
if (!(EC_POINT_is_on_curve(ka->group, RA, ka->ctx))) {
printf("RA is not ECC point\n");
ret = NULL;
goto end;
}
BIGNUM *x1 = BN_new();
calc_x(ka, RA, &x1);
dump_bn("x1`:",x1);
unsigned char kdfbuf[128] = {0};
EC_POINT *point = EC_POINT_new(ka->group);
BN_CTX *bnctx = BN_CTX_new();
BIGNUM *h = BN_new();
EC_GROUP_get_cofactor(ka->group, h, bnctx);
BN_mul(h, h, t, bnctx);
EC_POINT_mul(ka->group, point, NULL, RA, x1, bnctx);
EC_POINT_add(ka->group, point, point, PA, bnctx);
EC_POINT_mul(ka->group, point, NULL, point, h, bnctx);
if (EC_POINT_is_at_infinity(ka->group, point)) {
printf("V is 0 point\n");
ret = NULL;
goto end;
}
printf("点V:\n");
dump_point(ka, point);
unsigned char agreekey[16]={0};
gen_kdf(ka, point, Z_peer, agreekey, 0);
dump_hex("agreement key:",agreekey,16);
ret = ka->R;
end:
BN_free(x);
BN_free(t);
BN_free(x1);
BN_free(h);
EC_POINT_free(point);
return ret;
}
发起方A
int gen_key(SM2KA *ka, EC_POINT *RB, EC_POINT *PB, unsigned char *Z_peer)
{
int ret = 0;
BIGNUM *x = BN_new();
BIGNUM *t = BN_new();
calc_x(ka, ka->R, &x);
BN_mod_mul(t, x, ka->r, ka->order, ka->ctx);
BN_mod_add(t, t, ka->prik, ka->order, ka->ctx);
if (!(EC_POINT_is_on_curve(ka->group, RB, ka->ctx))) {
printf("RB is not ECC point\n");
ret = -1;
goto end;
}
calc_x(ka, RB, &x);
unsigned char kdfbuf[128] = {0};
EC_POINT *point = EC_POINT_new(ka->group);
BN_CTX *bnctx = BN_CTX_new();
BIGNUM *h = BN_new();
EC_GROUP_get_cofactor(ka->group, h, bnctx);
BN_mul(h, h, t, bnctx);
EC_POINT_mul(ka->group, point, NULL, RB, x, bnctx);
EC_POINT_add(ka->group, point, point, PB, bnctx);
EC_POINT_mul(ka->group, point, NULL, point, h, bnctx);
if (EC_POINT_is_at_infinity(ka->group, point)) {
printf("V is 0 point\n");
ret = -1;
goto end;
}
printf("点U:\n");
dump_point(ka, point);
unsigned char agreekey[16]={0};
gen_kdf(ka, point, Z_peer, agreekey, 1);
dump_hex("agreement key:",agreekey,16);
end:
BN_free(x);
BN_free(t);
BN_free(h);
EC_POINT_free(point);
return ret;
}
源码测试数据
按照《GMT 0003.5-2012 SM2椭圆曲线公钥密码算法第5部分:参数定义》中密钥交换的测试参数,通过测试,和其中协商结果密钥一致。
=======================================
密钥协商初始化:
=======================================
ZA:
0x3b, 0x85, 0xa5, 0x71, 0x79, 0xe1, 0x1e, 0x7e, 0x51, 0x3a, 0xa6, 0x22, 0x99, 0x1f, 0x2c, 0xa7,
ZB:
0x79, 0xc9, 0x88, 0xd6, 0x32, 0x29, 0xd9, 0x7e, 0xf1, 0x9f, 0xe0, 0x2c, 0xa1, 0x05, 0x6e, 0x01,
=======================================
发送方A:
=======================================
ra:
0xd4, 0xde, 0x15, 0x47, 0x4d, 0xb7, 0x4d, 0x06, 0x49, 0x1c, 0x44, 0x0d, 0x30, 0x5e, 0x01, 0x24,
0x00, 0x99, 0x0f, 0x3e, 0x39, 0x0c, 0x7e, 0x87, 0x15, 0x3c, 0x12, 0xdb, 0x2e, 0xa6, 0x0b, 0xb3,
点RA
-X
0x64, 0xce, 0xd1, 0xbd, 0xbc, 0x99, 0xd5, 0x90, 0x04, 0x9b, 0x43, 0x4d, 0x0f, 0xd7, 0x34, 0x28,
0xcf, 0x60, 0x8a, 0x5d, 0xb8, 0xfe, 0x5c, 0xe0, 0x7f, 0x15, 0x02, 0x69, 0x40, 0xba, 0xe4, 0x0e,
-Y
0x37, 0x66, 0x29, 0xc7, 0xab, 0x21, 0xe7, 0xdb, 0x26, 0x09, 0x22, 0x49, 0x9d, 0xdb, 0x11, 0x8f,
0x07, 0xce, 0x8e, 0xaa, 0xe3, 0xe7, 0x72, 0x0a, 0xfe, 0xf6, 0xa5, 0xcc, 0x06, 0x20, 0x70, 0xc0,
=======================================
发送方B:
=======================================
rb:
0x7e, 0x07, 0x12, 0x48, 0x14, 0xb3, 0x09, 0x48, 0x91, 0x25, 0xea, 0xed, 0x10, 0x11, 0x13, 0x16,
0x4e, 0xbf, 0x0f, 0x34, 0x58, 0xc5, 0xbd, 0x88, 0x33, 0x5c, 0x1f, 0x9d, 0x59, 0x62, 0x43, 0xd6,
点RB
-X
0xac, 0xc2, 0x76, 0x88, 0xa6, 0xf7, 0xb7, 0x06, 0x09, 0x8b, 0xc9, 0x1f, 0xf3, 0xad, 0x1b, 0xff,
0x7d, 0xc2, 0x80, 0x2c, 0xdb, 0x14, 0xcc, 0xcc, 0xdb, 0x0a, 0x90, 0x47, 0x1f, 0x9b, 0xd7, 0x07,
-Y
0x2f, 0xed, 0xac, 0x04, 0x94, 0xb2, 0xff, 0xc4, 0xd6, 0x85, 0x38, 0x76, 0xc7, 0x9b, 0x8f, 0x30,
0x1c, 0x65, 0x73, 0xad, 0x0a, 0xa5, 0x0f, 0x39, 0xfc, 0x87, 0x18, 0x1e, 0x1a, 0x1b, 0x46, 0xfe,
x2`:
0xfd, 0xc2, 0x80, 0x2c, 0xdb, 0x14, 0xcc, 0xcc, 0xdb, 0x0a, 0x90, 0x47, 0x1f, 0x9b, 0xd7, 0x07,
tb:
0xd0, 0x42, 0x96, 0x37, 0xf5, 0xa6, 0xd5, 0xd1, 0xe6, 0xc5, 0x45, 0x23, 0x51, 0x69, 0xdf, 0x85,
0x23, 0x11, 0x63, 0x06, 0x0a, 0x65, 0x4e, 0xcb, 0xa0, 0xf6, 0x57, 0xfd, 0x62, 0x9e, 0x8d, 0xd9,
x1`:
0xcf, 0x60, 0x8a, 0x5d, 0xb8, 0xfe, 0x5c, 0xe0, 0x7f, 0x15, 0x02, 0x69, 0x40, 0xba, 0xe4, 0x0e,
点V:
-X
0xc5, 0x58, 0xb4, 0x4b, 0xee, 0x53, 0x01, 0xd9, 0xf5, 0x2b, 0x44, 0xd9, 0x39, 0xbb, 0x59, 0x58,
0x4d, 0x75, 0xb9, 0x03, 0x4d, 0xd6, 0xa9, 0xfc, 0x82, 0x68, 0x72, 0x10, 0x9a, 0x65, 0x73, 0x9f,
-Y
0x32, 0x52, 0xb3, 0x5b, 0x19, 0x1d, 0x8a, 0xe0, 0x1c, 0xd1, 0x22, 0xc0, 0x25, 0x20, 0x43, 0x34,
0xc5, 0xea, 0xcf, 0x68, 0xa0, 0xcb, 0x48, 0x54, 0xc6, 0xa7, 0xd3, 0x67, 0xec, 0xad, 0x4d, 0xe7,
agreement key:
0x6c, 0x89, 0x34, 0x73, 0x54, 0xde, 0x24, 0x84, 0xc6, 0x0b, 0x4a, 0xb1, 0xfd, 0xe4, 0xc6, 0xe5,
=======================================
发送方A:
=======================================
点U:
-X
0xc5, 0x58, 0xb4, 0x4b, 0xee, 0x53, 0x01, 0xd9, 0xf5, 0x2b, 0x44, 0xd9, 0x39, 0xbb, 0x59, 0x58,
0x4d, 0x75, 0xb9, 0x03, 0x4d, 0xd6, 0xa9, 0xfc, 0x82, 0x68, 0x72, 0x10, 0x9a, 0x65, 0x73, 0x9f,
-Y
0x32, 0x52, 0xb3, 0x5b, 0x19, 0x1d, 0x8a, 0xe0, 0x1c, 0xd1, 0x22, 0xc0, 0x25, 0x20, 0x43, 0x34,
0xc5, 0xea, 0xcf, 0x68, 0xa0, 0xcb, 0x48, 0x54, 0xc6, 0xa7, 0xd3, 0x67, 0xec, 0xad, 0x4d, 0xe7,
agreement key:
0x6c, 0x89, 0x34, 0x73, 0x54, 0xde, 0x24, 0x84, 0xc6, 0x0b, 0x4a, 0xb1, 0xfd, 0xe4, 0xc6, 0xe5,
SM2密钥协商流程正确性分析
密钥协商的原理是双方通过KDF生成同样的密钥。以下是双方计算KDF的流程: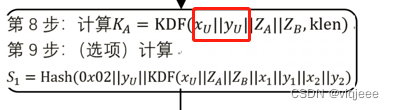
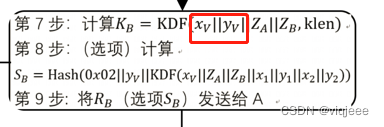
从双方计算流程看,主要靠双方计算的U点和V点是否一致
以下分析双方计算的U点和V点是否一致。
发起方A
U=(h*Ta)*(PB+Xb*Rb)
其中
Ta=(da+Xa*ra)
Rb=rb*G
带入Ta,h为1
U=(da+Xa*ra)(PB+Xb*Rb)
= (da+Xa*ra)(db+Xb*rb)G
=V
响应方B
V=(h*Tb)*(PA+Xa*Ra)
其中
Tb=(db+Xb*rb)
Ra=ra*G
带入Tb,h为1
V=(db+Xb*rb)(PA+Xa*Ra)
= (db+Xb*rb)(da+Xa*ra)G
更多推荐
 已为社区贡献4条内容
已为社区贡献4条内容









所有评论(0)